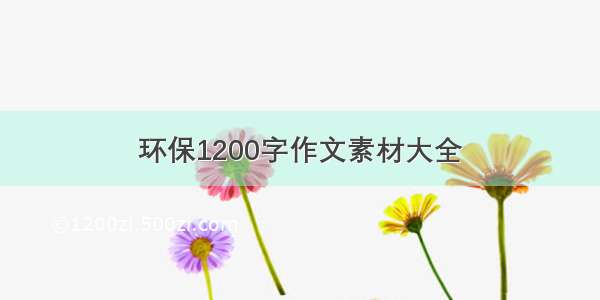
Suricata支持DDOS流量检测模型
What
分布式拒绝服务(Distributed Denial of Service,简称DDoS)将多台计算机联合起来作为攻击平台,通过远程连接利用恶意程序,对一个或多个目标发起DDoS攻击,消耗目标服务器性能或网络带宽,从而造成服务器无法正常地提供服务。
How
通常,攻击者使用一个非法账号将DDoS主控程序安装在一台计算机上,并在网络上的多台计算机上安装代理程序。在所设定的时间内,主控程序与大量代理程序进行通讯,代理程序收到指令时对目标发动攻击,主控程序甚至能在几秒钟内激活成百上千次代理程序的运行。
Classification
Suricata Rules
tcp畸形报文TCP报文标志位包括URG、ACK、PSH、RST、SYN、FIN。攻击者通过发送非法TCP flag组合的报文,受害主机收到后进行判断识别,消耗其性能,甚至会造成有些操作系统报文处理异常,主机崩溃。
alert tcp $EXTERNAL_NET any -> $HOME_NET any (msg:"GPL SCAN nmap fingerprint attempt";flags:SFPU; flow:stateless;reference:arachnids,05; classtype:attempted-recon; sid:2100629; rev:7; metadata:created_at _09_23, updated_at _09_23;)
teardrop攻击
攻击者截取IP数据包后,把偏移字段设置成不正确的值,接收端在收到这些分拆的数据包后,就不能按数据包中的偏移字段值正确组合出被拆分的数据包,这样,接收端会不停的尝试,以至操作系统因资源耗尽而崩溃
alert tcp $EXTERNAL_NET any -> $HOME_NET any (msg:"ET EXPLOIT Invalid non-fragmented packet with fragment offset>0";fragbits: !M; fragoffset: >0;reference:url,/bin/view/Main/2001022;classtype:bad-unknown; sid:2001022; rev:5; metadata:created_at _07_30, updated_at _07_30;)
smurf攻击
攻击者向网络中的广播地址发送源IP伪造为受害者的ICMP请求报文,使得网络中的所有主机向受害者回应ICMP应答报文,这样造成受害者系统繁忙,链路拥塞
alert ip any any <>127.0.0.0/8any (msg:"GPL SCAN loopback traffic"; reference:url,/firewall/egress.php;classtype:bad-unknown; sid:2100528; rev:6; metadata:created_at _09_23, updated_at _08_20;)
land攻击
Land攻击是指攻击者向受害者发送TCP报文,此TCP报文的源地址和目的地址同为受害者的IP地址。这将导致受害者向它自己的地址发送SYN-ACK回应报文,结果这个地址又发回ACK消息并创建一个空连接。从而造成资源的消耗。
alert tcp$HOME_NET any -> $HOME_NETany (msg:"ET MALWARE APT 41 LOWKEY Backdoor [TCP Relay Module] - TCP Relay Successfully Activated on New Host";flow:established,to_server; content:"|00 00 00 00 00 D4 00 00 00 00 00 00 00 00 00 00|";reference:url,/blog/threat-research//10/lowkey-hunting-for-the-missing-volume-serial-id.html;classtype:command-and-control; sid:2028888; rev:1; )
ping of death
攻击者A向受害者B发送一些尺寸超大的ICMP
alerticmp$EXTERNAL_NET any -> $HOME_NET any (msg:"GPL ICMP Large ICMP Packet";dsize:>800; itype:8;reference:arachnids,246; classtype:bad-unknown; sid:2100499; rev:5; metadata:created_at _09_23, updated_at _09_23;)
syn flood
恶意的向某个服务器端口发送大量的SYN包,则可以使服务器打开大量的半开连接,分配TCB,从而消耗大量的服务器资源,同时也使得正常的连接请求无法被响应。而攻击发起方的资源消耗相比较可忽略不计。
alert tcp $EXTERNAL_NET 10000: -> $HOME_NET 0:1023 (msg:"ET DOS Potential Tsunami SYN Flood Denial Of Service Attempt";flags:S; flow:to_server; dsize:>900; threshold: type both, count 20, seconds 120, track by_src;reference:url,/uploadedFiles/Resources_and_Content/Threat/TsunamiSYNFloodAttack.pdf;classtype:attempted-dos; sid:404; rev:3; metadata:created_at _10_15, updated_at _10_15;)
udp flood
UDP Flood属于带宽类攻击,向目标服务器发起大量的UDP报文,这种UDP报文通常为大包,且速率非常快,通常会造成以下危害:消耗网络带宽资源,严重时造成链路拥塞;大量变源变端口的UDP Flood会导致依靠会话转发的网络设备,性能降低甚至会话耗尽,从而导致网络瘫痪。
alert udp $EXTERNAL_NET any -> $HOME_NET 5060 (msg:"ET VOIP INVITE Message Flood UDP";content:"INVITE"; depth:6; threshold: type both , track by_src, count 100, seconds 60;reference:url,/698;classtype:attempted-dos; sid:698; rev:1; metadata:created_at _07_30, updated_at _07_30;)
icmp flood
短时间内向特定目标不断请求 ICMP 回应,致使目标系统负担过重而不能处理合法的传输任务,就发生了 ICMP Flood。
alert icmp any any -> any any (msg:"ET DOS Microsoft Windows 7 ICMPv6 Router Advertisement Flood";itype:134; icode:0; byte_test:1,&,0x08,2; content:"|03|"; offset:20; depth:1; byte_test:1,&,0x40,2,relative; byte_test:1,&,0x80,2,relative; threshold:type threshold, track by_src, count 10, seconds 1;reference:url,http://www.samsclass.info/ipv6/proj/proj8x-124-flood-router.htm;classtype:attempted-dos; sid:996; rev:3; metadata:created_at _07_02, updated_at _07_02;)
dns quert flood
多台傀儡机同时发起海量的域名查询请求,服务端无法响应正常的Query请求,从而导致拒绝服务。
alertdns$HOME_NET any -> any any (msg:"ET MALWARE Likely Linux/Tsunami DDoS Attack Participation (s-p-o-o-f-e-d.h-o-s-t.name)";threshold:type limit,track by_src,count 3,seconds 60; dns.query; content:"s-p-o-o-f-e-d.h-o-s-t.name"; depth:26; fast_pattern; nocase; endswith;reference:md5,c01991d55133d0057c9b721bb141a5d9; classtype:trojan-activity; sid:691; rev:5; metadata:created_at _08_19, former_category CURRENT_EVENTS, updated_at _09_17;)
slowloris
攻击者在HTTP请求头中将Connection设置为Keep-Alive,要求Web Server保持TCP连接不要断开,随后缓慢的每隔几分钟发送一个key value格式的数据到服务端,如a:b\r\n,导致服务端认为HTTP头部没有接收完成而一直等待。如果攻击者使用多线程或者傀儡机来做同样的操作,服务器的WEB容器很快就被攻击者占满了TCP连接而不再接受新的请求。
alert http $EXTERNAL_NET any -> $HTTP_SERVERS any (msg:"ET SCAN Simple Slowloris Flooder";flow:established,to_server; threshold:type limit, track by_src, count 1, seconds 300; http.method; content:"POST"; http.header; content:"Content-length|3a 20|5235|0d 0a|"; fast_pattern; http.header_names;content:!"User-Agent|0d 0a|"; reference:url,/docs/HII_Denial_of_Service_Attacks-Trends_Techniques_and_Technologies.pdf;classtype:web-application-attack; sid:033; rev:5; metadata:created_at _12_13, updated_at _05_08;)
cc攻击
针对 Web 服务在第七层协议发起的攻击,正常的有效的数据包 不断发出针对不同资源和页面的 HTTP 请求,并尽可能请求无法被缓存的资源(DB查询等),这样就极大加重了服务器的计算和IO资源,从而导致瘫痪
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:"ET DOS LOIC Javascript DDoS Outbound";flow:established,to_server; threshold: type both, track by_src, count 5, seconds 60; http.method; content:"GET"; http.uri; content:"/?id="; fast_pattern;depth:5; content:"&msg="; distance:13; within:5; pcre:"/^\/\?id=[0-9]{13}&msg=/"; reference:url,/diary/Javascript+DDoS+Tool+Analysis/12442;reference:url,/threatlevel//01/anons-rickroll-botnet;classtype:attempted-dos; sid:141; rev:6; metadata:created_at _01_23, updated_at _05_06;)
Suricata 支持ddos流量模型的Option
tcp.flagsdetect which flags are set in the TCP header#define TH_FIN 0x01#define TH_SYN 0x02#define TH_RST 0x04#define TH_PUSH0x08#define TH_ACK 0x10#define TH_URG 0x20
fragbits,fragoffset
check if the fragmentation and reserved bits are set in the IP headermatch on specific decimal values of the IP fragment offset field
itype, icode
match on a specific ICMP type/code TYPECODEDescription00Echo Reply——回显应答(Ping应答) 30Network Unreachable——网络不可达 31Host Unreachable——主机不可达 32Protocol Unreachable——协议不可达 33Port Unreachable——端口不可达 34Fragmentation needed but no frag35Source routing failed——源站选路失败 36Destination network unknown——目的网络未知 ... ...
flow
match on direction and state of the flowestablished/not established For TCP a connection will be established after a three way handshake.For other protocols (for example UDP), the connection will be considered established after seeing traffic fromboth sides of the connection.
threshold
control the rule's alert frequencythreshold: type <threshold|limit|both>, track <by_src|by_dst>, count <N>, seconds <T>A threshold setting of N means on the Nth time the rule matches an alert is generated.If set to limit N, it alerts at most N times.
byte_test
extract <num of bytes> and perform an operation selected with <operator> against the value in <test value> at a particular <offset>data = DetectBytetestParse("4 , ! &, 5, 0 , little ", NULL, NULL);((data->op == DETECT_BYTETEST_OP_AND)&& (data->nbytes == 4)&& (data->value == 5)&& (data->offset == 0)&& (data->neg_op)&& (data->flags == DETECT_BYTETEST_LITTLE)&& (data->base == DETECT_BYTETEST_BASE_UNSET))
dns.query,http.header,http.method,http.uri
content modifiers
dsize,depth,distance,within
match on the size of the packet payloadhow many bytes from the beginning of the payload will be checkeddistance 两个content距离within 两个content尾的距离